IRM Technical Consultant, Matthew Twells, has written a blog on the basics of 5G technology and some of the 5G cybersecurity risks.
Quick overview of 5G: What is it?
5G is an extremely similar communications system to the existing 4G LTE cellular network in place that powers a considerable share of mobile communications in the UK and worldwide.
It operates (for any radio nerds out there) over the LTE range of 600MhZ – 6GhZ and over a millimetre wave spectrum of 24-86 Ghz.
In its simplest form , analogue signals representing pictures / sounds etc. are digitised on the originating phone/ tablet/computer and transmitted as bits over a cellular network of base stations and what are essentially radio antennae.

Above is a representation of a network of “cells” , each one broadcasting and carrying data of many kinds for a small geographic area – together they comprise a “cellular network” covering a much wider distance.
This is roughly the model over which 3G and later 4G LTE work to carry your Facebook status updates and your cat videos to and from your phone when you’re waiting for the bus – all 5G devices will communicate by radio wave to an array of antennae and low power automatic transceivers (able to receive and transmit data rather than just one of these functions) and then connect that to the regular Internet via plugging in via a fibre-optic cable or wireless transfer.
As you move from one cell to another, you’re seamlessly handed off to the nearest antenna in the neighnouring cell you just entered , so you won’t notice on your device.
What can 5G do that 4G couldn’t?
5G , as briefly mentioned above has plans to utilise a new spectrum or slice of the radio frequency spectrum to send and receive data over called the millimetre wave, so named because when you’re transmitting at 24GhZ and above, the size of the radio wave carrying your data is only millimetres wide , and the antennae broadcasting and receiving them are only centimetres long.
This lets 5G do a bunch of cool stuff that 4G couldn’t in a feasible way.
MIMO (Multiple Input, Multiple Output) is one of these things.
The antennae in your phone will be small enough that 5G devices will have more than one and there will be more than one in your local cell too – so you can send and receive data at speeds that current networks just can’t compete with – 1Gb/s+ wi-fi and data everywhere you go!
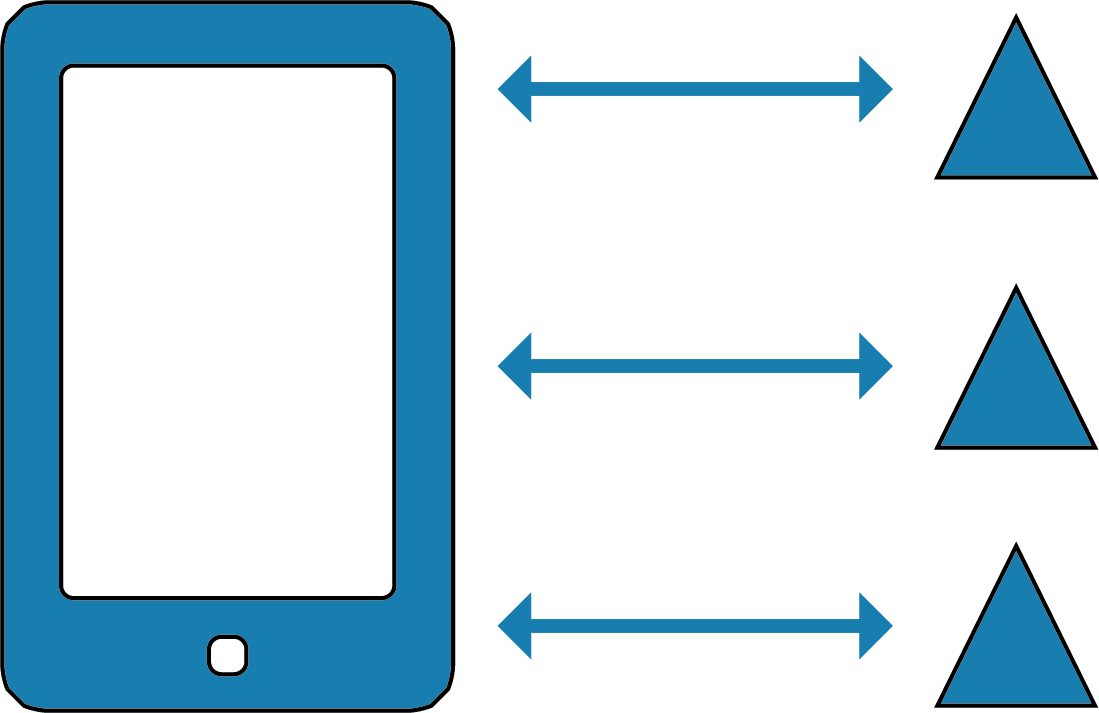
Represented by the above diagram, MIMO essentially makes all of the little 5G antennae in your phone / in your geographic area work in parallel as a phased array to transfer files way faster than was possible before. Each of those arrows is transferring parts of the same file or are processing the same connection – hence the Multiple Input, Multiple Output.
This is where the super-fast data transfer speeds come from that everyone is talking about.
Beamforming is another cool thing 5G can and will be doing. This is where the base station in each cell (essentially a “home” computer managing all the antennae in a given area) continually monitors and calculates the best route for radio waves to reach a given device – and alternate routes for transfer if any antenna goes down.
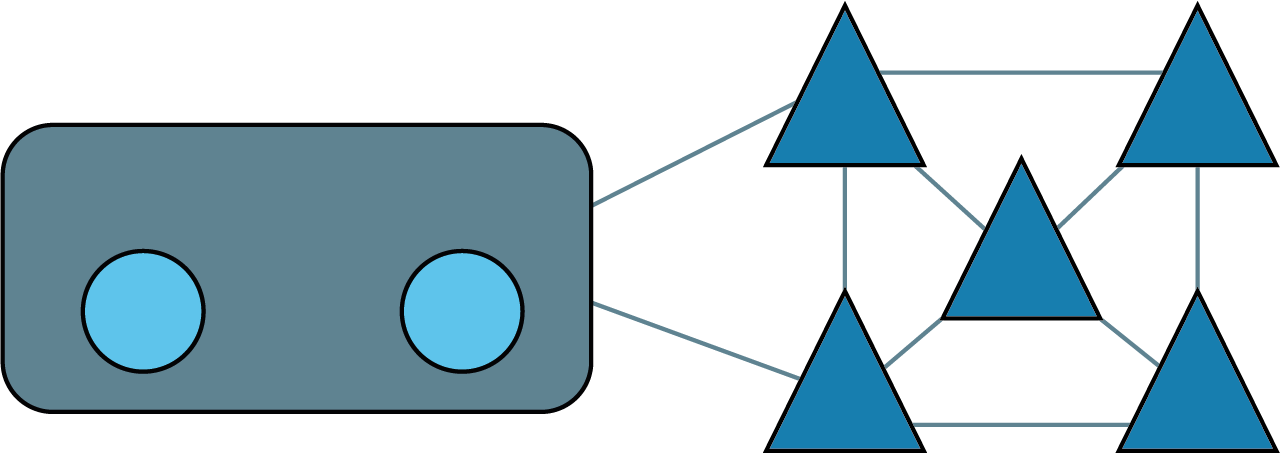
Millimetre wave “beams” under beamforming technology will be fired along a path of antennae constantly calculated to be the fastest way to get to a given point. Every antenna is connected up – much like routers in a regular IT network.
This will (hopefully) deliver latency at far lower rates than current networks can deliver, which will improve user experience for all involved and make feasible new forms of computing and distributed processing.
Mobile Edge Computing is another development coming with 5G that should bring a fascinating raft of new applications along with it. Mobile edge computing is where either parts of an application’s functionality or its content are stored on MEC application servers at 5G base stations. This means that when accessed, the application can serve content far faster and make use of a distributed grid of nearby base stations to serve content and process data much faster than the old method – which was to serve content from a regional or even central server.
This could support real-time super-high-definition multiplayer mobile gaming or new forms of application that require real-time communications that the current network cannot currently provide.
This will also make use of 5G Network Slicing , a method of slicing a physical network infrastructure into multiple end-to-end virtualised logical networks and multiplexing them – allowing one physical connection to support many many more services than previously possible.
What are the 5G cybersecurity risks (and other risks)?
Much like any other major technological development, 5G brings with it a raft of potential and very real concerns that need to be addressed as the technology quickly gains adoption worldwide. So what are some of the top 5G cybersecurity risks?
- Exploding Attack Surface : The number of networked devices (IoT) is set to enter the billions within the next decade and every single one of them is a potential breach point. Security in design and in the underlying code-base will become an increasing priority for security professionals as the target range will be getting gigantic.
- Immature Tech / Insufficient Testing: 5G , it is safe to say, is being adopted very quickly and it has been brought up by many industry bodies that 5G is too immature a technology to go into such wide adoption before more testing and security reviews can be done. However, many infrastructure upgrades and budgets have already been committed , creating a “too late now” mentality.
- Reliance by Mission-critical Applications: The way that 5G works will bring with it a new method of serving content and processing data that means a significant proportion of the computing load is handled at the edge of the network rather than centrally. Bringing the concern with it of “what happens when the edge network goes down?” – especially when very little or potentially none of the application is processed centrally.
- Potentially Gigantic Botnets/DdoS Potential: With billions of networked devices out there , all with the capability to send and receive traffic, the possibility of placing a command-and-control persistent backdoor on multiple devices and targeting traffic to a victim endpoint grows to terrifying capabilities. The potential to bring larger and larger services and organisations down comes along with the larger and larger adoption of the technology by manufacturers and network service providers.
Interference: The spectrums used by 5G are very near and overlap with the same spectrum used by a class of satellites known as passive remote sensing satellites. The issue is that these satellites are used for weather monitoring and prediction around the world and the potentially massive amount of interference on that frequency band could result in predictions being less accurate than previously.
Millimetre Wave: The miillimetre wave bands used by 5G are the exact same used by a developing breed of crowd control and riot suppression technology that makes use of millimetre waves to cause large enough irritation and discomfort in the victim to hopefully discourage further violent behaviour. Having a distributed grid of thousands of networked millimetre wave antennae brings with it concerns on whether that grid could be employed in such a way, as they already function very similarly.
Surveillance: There has been much debate and drama around the world regarding the security of the devices facilitating the 5G network – much of it centring around the Chinese telecoms giant Huawei and its perceived allegiance to Chinese intelligence services.
Want to learn more about 5G cybersecurity risks? Soon, IRM will be publishing a guidance paper on this topic. Keep an eye on our social media and website to be able to download the content.
