What is the vulnerability?
A critical vulnerability within Citrix Application Delivery Controller (ADC) and Citrix Gateway is actively being exploited in the wild. Exploits allowing for remote code execution have been published allowing for complete take over of the Citrix devices.
The public exploits have been disclosed ahead of a security patch from Citrix. According to Shodan, there are currently 126,331 Citrix ADC or Gateway hosts publicly accessible which could be exploited, if mitigations have not already been put in place.
The vulnerability is a directory traversal bug which calls a perl script that is used to append files in an XML format to the vulnerable host. This, in turn, allows for remote code execution; allowing a malicious attacker to execute code and subsequently compromise the data stored on the device.
How was it discovered?
Mikhail Klyuchnikov of Positive Technologies, and Gianlorenzo Cipparrone and Miguel Gonzalez of Paddy Power Betfair plc identified this vulnerability and reported it to Citrix.
The vulnerability affects all supported product versions and all supported platforms:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
What is the potential impact of the vulnerability?
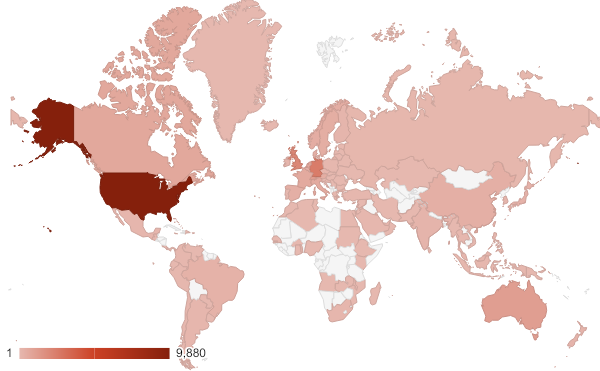
Using data provided by BinaryEdge, vulnerable hosts were found in 122 countries around the world. Analysis of this data found that this vulnerability currently affects; military, government, banking, healthcare and major utility systems. Various public exploits have now been published, allowing for trivial compromise. Exploitation of this vulnerability could be used to compromise sensitive data, spread ransomware or weaponise multiple devices for Distributed Denial of Service (DDoS) attacks. The following graphic provides a breakdown of affected devices across the world.
What fix has been put in place?
Citrix expects to have firmware updates in the form of refresh builds to be available across all supported versions of Citrix ADC and Citrix Gateway before the end of January 2020. The following configuration change published by Citrix can be made to serve as a mitigation until the official patch is released: https://support.citrix.com/article/CTX267679
