$11m demanded in EDP ransomware attack
The European utility organisation, EDP, has fallen victim to a demand for $11 million in a ransomware attack this week.
EDP is based in Portugal and is the majority owner of one of the world’s largest wind power operators.
The EDP ransomware attack is thought to be fuelled by the “Ragnar Locker” variant, enabling the criminals to gain access to systems and demanding payment within 20 days to prevent the release of sensitive information. The ransom note left (see picture below) threatened to publish 10TB of data from the company’s file servers or sell it to ‘interested parties’ if they failed to pay.
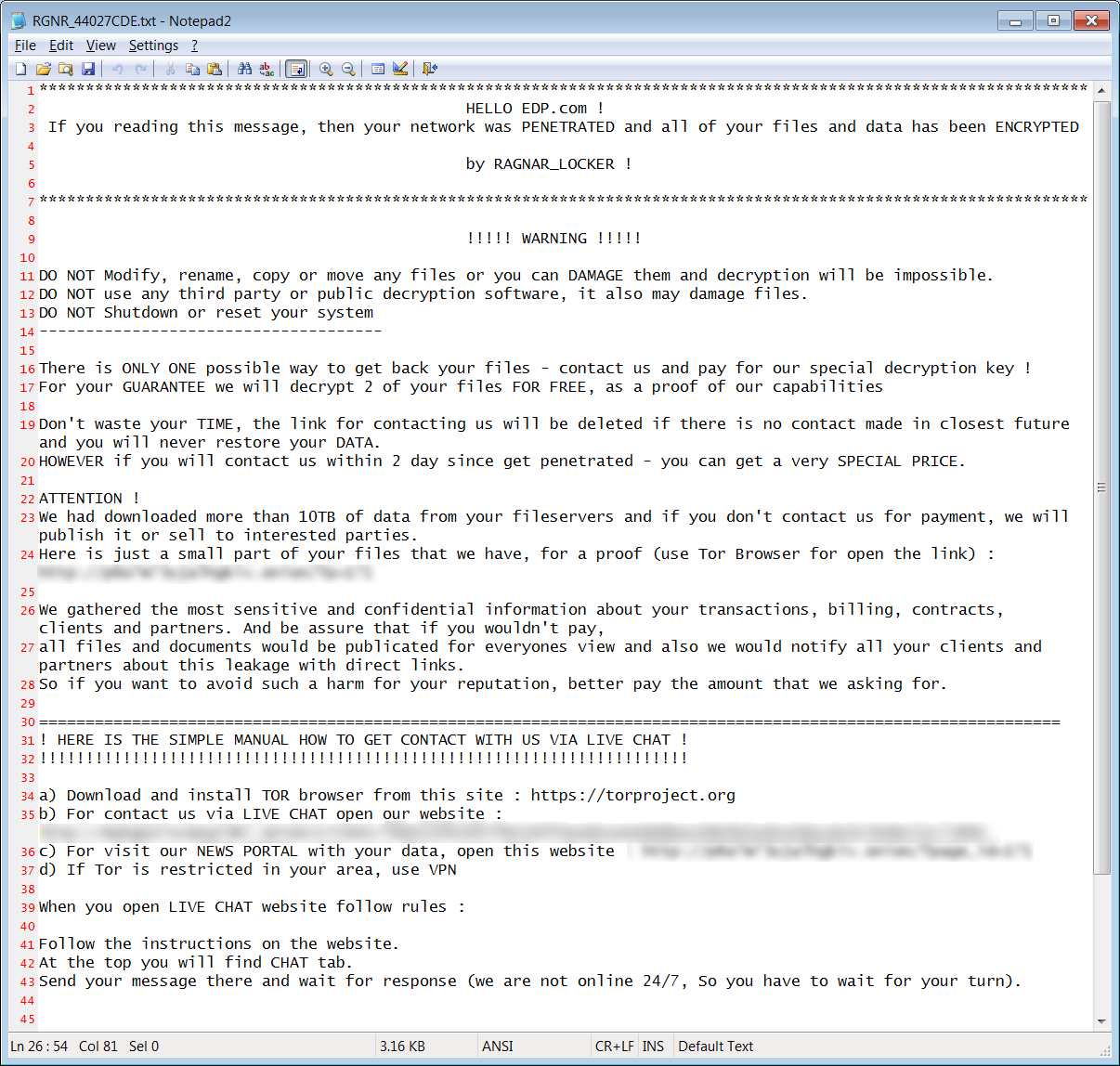
The company has confirmed the breach but states that the energy supply has not been affected.
You can read more here.
Singapore ranked first in ‘cybersecurity readiness’
In a survey prepared by Deloitte, Singapore has been named as top-ranking in the Asia Pacific region for cybersecurity readiness.
Whilst Singapore has always been a top target for criminals due to its highly-developed digital economy, the country has plenty of legislation in place to protect businesses.
What factors were considered in the survey? Size of the attack surface, frequency of attacks, estimated value being risked and the preparedness through policy-making and legislation.
Ultimately, Singapore’s understanding of its cybersecurity threat and its willingness to continuously invest in cyber funding has made it more effective in handling cyber-attacks and threats.
You can read more here.
US Defence Department fails to meet cybersecurity targets
 According to a report by the Government Accountability Office (GAO) in America, the Department of Defense (DOD) has failed to implement three key initiatives aimed to improve ‘cybersecurity hygiene’.
According to a report by the Government Accountability Office (GAO) in America, the Department of Defense (DOD) has failed to implement three key initiatives aimed to improve ‘cybersecurity hygiene’.
Three department-wide initiatives were identified several years ago and here’s a breakdown of how the Department is faring:
- The 2015 Culture and Compliance Initiative: Eleven tasks including cyber education and training, and making recommendations to organisations on how to improve their cyber capabilities. Seven out of the eleven haven’t been fully implemented.
- The 2015 Cyber Discipline Plan: Seventeen tasks designed to remove preventable vulnerabilities from the DOD networks which could otherwise compromise systems. Four of the tasks have not been completed despite targets set at 90% implementation.
- Cyber Awareness Training: Created to help enhance the knowledge and awareness of cybersecurity amongst the DOD workforce. Six components were identified where the DOD had no information on whether users had completed the necessary training at all.
The GAO has recommended that the DOD should ensure steps are taken to complete the planned tasks. If not completed, the DOD faces an enhanced risk of successful attack.
You can read more here.
Shipping company website shutdown by cyber-attack
The world’s second largest container line, the Mediterranean Shipping Company, experienced a network outage over the Easter weekend due to a malware attack.
The Geneva headquarters were victim to a malware attack which caused the booking system and website to shut down.
The company stated: “After a thorough investigation, we confirmed that it was confined to a limited number of physical computer systems in Geneva only and we determined that it was a malware attack based on an engineered targeted vulnerability.”
The company, at this stage, is not aware of any compromised data as a result of the incident.
You can read more here.
Quick-Fire Updates
Passwords stolen from San Francisco Airport: Hackers managed to compromise two of the airport’s websites during a cyber-attack, where it’s thought Windows login credentials were stolen. Users affected have been told to update their credentials. Read more here.
Online betting company sets aside $30m for cybersecurity claims: After SBTech’s cybersecurity incident in March, the company has set aside the large sum. This has been agreed during a merger with DraftKings, in the hope to cover any claims relating to the incident. Read more here.
