The Coronavirus (COVID-19) pandemic has created a huge surge in remote working across the world. This presents new cybersecurity challenges which must be managed. One of IRM’s Principal Security Consultants, Martin Needs, shares insight on the risks and mitigations.
ZOOM – REMOTE CONFERENCING
Zoom has exploded in usage since the pandemic, with schools, businesses and even local and central government holding meetings over the software. Zoom is currently facing privacy and security backlash from security experts, lawmakers and security services due to the insecure state of the default meeting configuration.
ENCRYPTION
Zoom states on its website and its security white paper that the application supports end-to-end encryption, this term refers to a way of protecting user data so that Zoom also has no access. However, an investigation revealed that Zoom secures video calls using Transport Layer Security (TLS) encryption. This is known as transport encryption, which is not end-to-end encryption. The Zoom service itself, or a malicious actor, should Zoom be compromised; could access the unencrypted video and audio content of Zoom meetings. This makes Zoom a target for hostile and state-sponsored actors.
ZOOMBOMBING
Each Zoom call has a randomly generated ID number between 9 and 11 digits long that is used to join the meeting. Research has identified that these meeting ID’s can be easily brute-forced and guessed to gain access to any meeting. Whilst this issue can be mitigated by setting a strong password to gain access to the meeting, this is not the current default setting within the software.
COMPROMISING CREDENTIALS
The Zoom Windows software is vulnerable to high-risk vulnerability in the client’s chat feature that could allow attackers to steal the Windows credentials. When sending a chat message, Zoom will convert Windows networking UNC paths into clickable links. If a user clicked this link, their encrypted Windows password hash could be transmitted to the malicious user. These password hashes could then be cracked and used to gain access to organisations externally accessible services, such as email or remote access software.
Zoom has made a statement stating they are working on addressing this vulnerability. However, its presence suggests that further high-risk issues may be present and further in-depth security testing is required.
COMPROMISING END-USERS
Recently, two vulnerabilities have been disclosed relating to the Zoom software on the Apple macOS operating system. The first vulnerability allows for a malicious user to gain the highest level of user privileges, known as ‘root’. This level of access would allow a malicious attacker to run malware or spyware without the end-users knowledge. The second issue allows for the hijacking of client webcam and microphone; a massive risk for business and government alike.
SECURITY AWARENESS
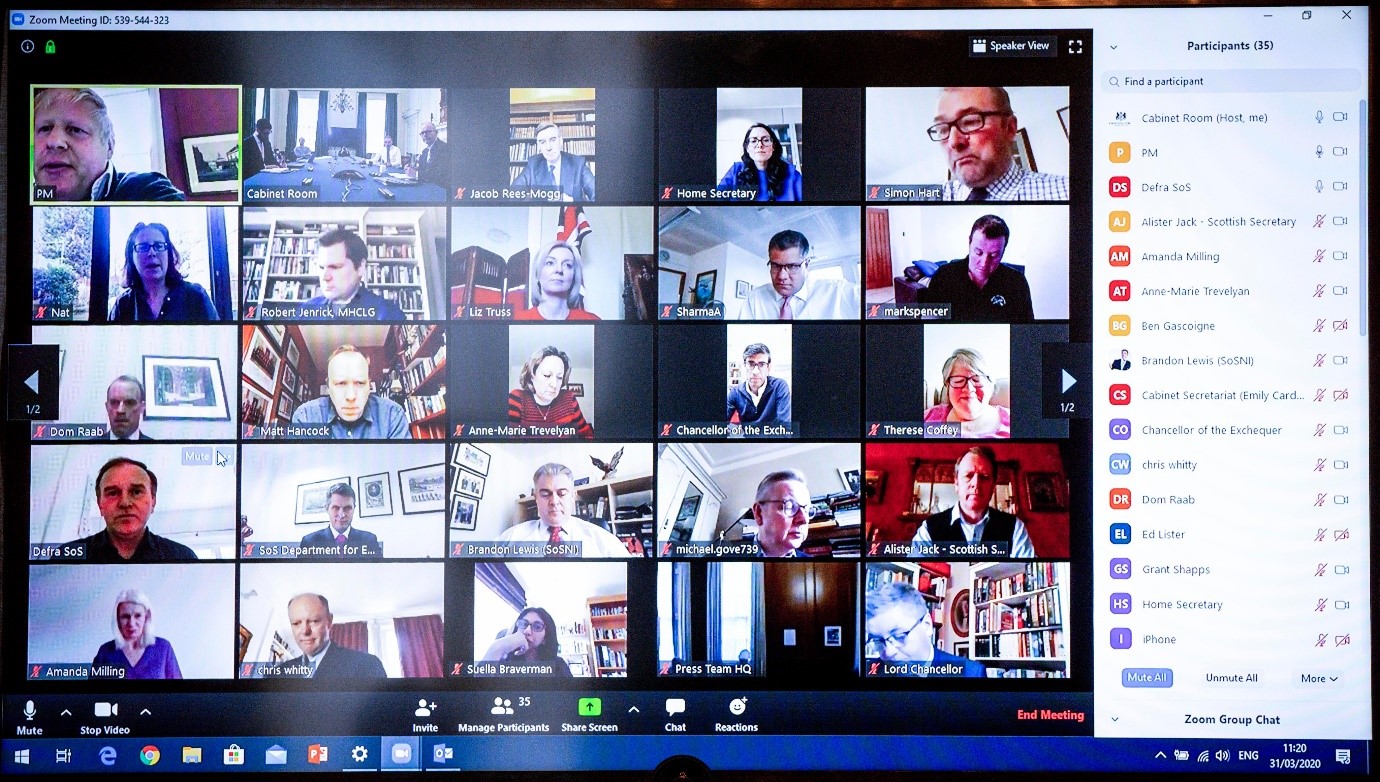
All staff should be practising good security awareness, this includes keeping software up-to-date, applying security patches and ensuring the confidentiality of data. Along with the spike in remote conferencing usage, there’s also been a spike in the public posting screenshots showing off their remote working solutions. This includes our PM, Boris Johnson, posting a screenshot of his Zoom meeting, disclosing the Zoom meeting ID required to connect to the meeting (see below)
REMOTE CONFERENCING RISK MITIGATION
CONTROL ACCESS
Most videoconferencing platforms allow for the creation of groups of users or the ability to restrict access by internet domain so only users with an email address from your company would be able to join the call. Alternatively, only allow attendees that are invited by adding their email addresses to the invite when scheduling the call.
Set a meeting password, typically an option when creating the meeting, which adds a randomly generated password that invitees will need to input.
Holding participants in a waiting room and approving the connection of each one gives the host ultimate control over who is in the meeting.
SECURITY BEST PRACTICES
It’s also important to give remote workers a refresher course in basic security best practice, taking time to make sure they know how to report any security issues. Workers should understand the importance of keeping software and devices up-to-date and patched. The training should also cover typical vectors which are being used by threats to compromise user devices.
EVALUATE AND TEST
Time should be taken to re-evaluate all the applications remote working employees will be using, such as chat and collaboration apps, video conferencing services, data sharing and remote access solutions. IRM can assist with this using our range of security testing services to ensure the applications and their configurations are secure.