Success requires a plan, it’s a long established truism:
FAIL TO PLAN = PLAN TO FAIL
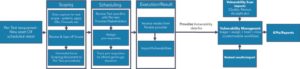
But, a plan is irrelevant if it is not executed in an effective and coherent manner… and this is especially true with regard to the management of your Penetration Testing process, where the investment in terms of both time and money are considerable. Most IT Security teams will have an established workflow that can be represented like this:
How can an IT Security team most effectively execute these elements of their workflow?
Scoping:
A well structured project data questionnaire, which can be shared directly with the relevant stakeholders, (and capture the details and evidence needed to create a clear requirement set that will be shared with Pen Test Providers) is an absolute must, but too often this first step in a Pen Test process is carried out over email and spreadsheets. This results in no real ownership (nor visibility) of the process, and can result in frustrating administrative delays, that can impact on the security of the overall project.
Scheduling:
Creating a detailed and coherent document, that can be shared with Pen Test Providers, is incredibly important. This ensures Pen Test engagements are scoped (and priced!) accurately. At the scheduling stage, it is also important to clarify any/all pre-requisites and be able to make appropriate arrangements; the most common complaint in regard to Pen Test engagements, is the failure to co-ordinate pre-reqs, resulting in testers unable to begin an engagement as system/network access rights etc are belatedly awarded. This has direct implications on the value and output of any testing arranged.
Results:
Too often the work of an IT Security team can get overlooked – creating clear reportable data from the constant stream of test results can become a Sisyphean task, and that is without the management of the vulnerabilities themselves. Having a central Pen Test portal, allows for all Pen Test Vulnerabilities to be:
- Imported
- Reviewed
- Remediated
- Reported
This streamlines an otherwise unwieldy process, while ensuring that the visibility and ownership that you try to establish at the start of a Pen test engagement, can be carried through to closure.
—————————————————————————————————————————————————
IRM’s cyber GRC platform, SYNERGi, now includes the Pen Test Management module; designed to support the workflow described and overcome the difficulties highlighted, allowing the effective execution of your Penetration Testing process.
Using a central repository (supported by a calendar) for all your Penetration tests, you can create specific Pen Test records, centralising Stakeholders, Test Owners & Test Providers, alongside the key project data.
This is supported by our Questionnaire builder, providing clear, detailed instructions on how to supply the information required to ensure accurate scoping for any type of test.
Questionnaires can be designed to ensure relevant sections go to relevant stakeholders, the use of logic mapping can avoid time spent reviewing questions that are not applicable to the project and SYNERGi will automatically chase for response inline with the requirements laid out, removing further administrative burdens from your workload.
Speaking of removing administrative burdens; SYNERGi’s response mapping feature allows you to populate a scoping document with the click of a single button; the relevant information from the Pen Test Record and Questionnaire response will be presented within the Proposal template of your choice; this can be shared with your audience of Pen Test Providers.
Having a Pen Test Record provides a central point where Pre-Req’s once established can be compiled, and ownership and deadlines for arrangements can be set.
Once the test has been delivered, importing, reviewing and remediating the Vulnerabilities remains your key focus, SYNERGi’s Pen Test Management portal enables you to:
- Undertake Severity assessment
- Link multiple Vulnerabilities
- This supports
- Prioritisation of Remediation Actions, alongside:
- Setting SLA targets for High, Medium and Low severity findings
Similarly, Remediation Actions themselves are linked to the Pen Test Record, or, if your approach is more granular, the Vulnerability Tasks.
The SYNERGi Pen Test Management Module supports the 4 R’s of Vulnerability Management:
1. Record
2. Review
3. Remediate
4. Re-Test
This gives you the opportunity to present a simple, yet meaningful overview of IT Security.

For more information contact us at: hello@irmsecurity.com
By Michael Wager – SYNERGi Training & Account Liaison Manager