IRM has grown from a boutique consultancy founded in 1998 to become Altran’s World Class Center for Cybersecurity. As an organisation, therefore, we have a genuine appreciation for the growth of this industry and we understand that most organisation’s cybersecurity budgets haven’t grown at the same pace. More importantly, irrespective of the specific industry that an organisation is in, most are seeing the same issues (though fixing them gets more complicated, the bigger the organisation!)
Our history and scale allows us to gather real insight. Our Risky Business Report released at the end of last year surveyed cybersecurity and risk management decision makers. Some of the issues raised in that report help inform our topic today, mainly:
91% of respondents agreed that an increased awareness at C-level is influencing decision making.
However, most respondents did offer the caveat that the C-Suite is still not as security aware as it needs to be. Decisions tend to lean to what the accountants require, rather than what is most safe for the business.
From the responses gathered, the majority of the budget made available is spent on firewalls, endpoint protection tools and anti-spam security…

The above picture summarises the reality of why managing risk and compliance within that landscape is so complicated.
The report also indicated that there is no established process for supplier assessments. More worryingly, only 9% of respondents were clear on how much data they share with suppliers!
Eliminating vendors is not an option, because it simply is not a realistic solution.
The reality of what we are seeing and hearing relates to an ever increasing volume of work; endless assessments and audits, some created by, almost all hindered by, a lack of visibility of the actions of other departments. Predominantly manual processes exacerbate this along with siloed GRC tools and reporting.
Improvements can be made through change and integration. Before we can deliver those outcomes, we have to be clear that security cannot own every process in the business. Doing this would simply compound the disproportionate degree of responsibility to resource.
If you are reading this, you likely have an accountability for building frameworks and reporting cyber/information risk to boards, customers, employees and/or stakeholders; and as such will be familiar with these challenges:
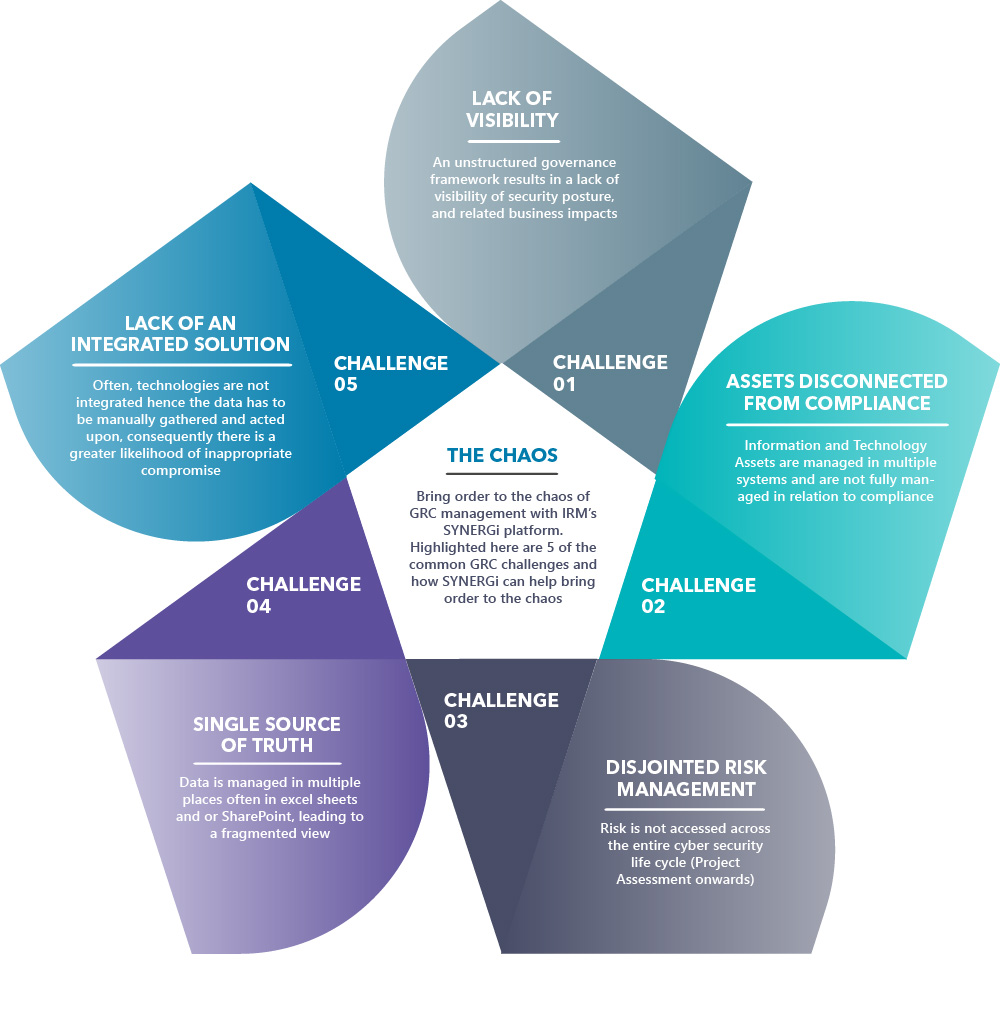
Adopting an integrated approach with GRC tools can allow you to form a ‘single source of truth’, you’ll be able to model your organisation within the tool. You will gain the ability to:
- easily present your organisational structure
- identify where your informational assets sit
- see what risks they are exposed to
- understand how those assets can be exposed
- view what controls you have in place to protect them
- analyse the risk & compliance assessments that provide evidence of their efficacy.
Establishing that clear picture of the operational realities, also allows you to populate organisational policies and objectives, tying compliance control activities to your organisational policies, and the operational risks to organisational objectives… this is a major step in ensuring Operational reality informs Enterprise policy.
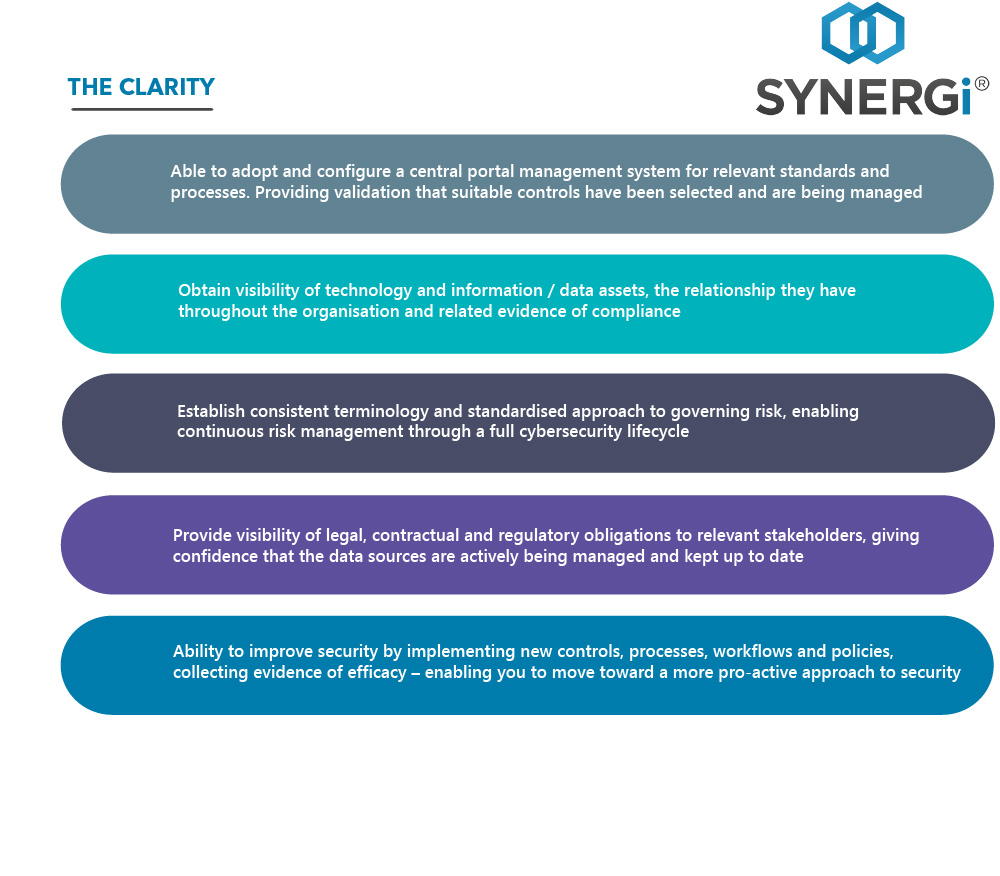
To learn more about IRM’s GRC tools, visit our page about the SYNERGi GRC Platform.
